By Gaurav Shekhar – Linkedin profile
Abstract: The proliferation of multi-cloud environments has introduced complexities in managing security policies and enforcing consistent protection against evolving cyber threats. Zero Trust Architecture (ZTA) has emerged as a crucial framework to address these challenges. This paper discusses the importance of ZTA in multi-cloud settings, outlining its benefits, advantages, and potential disadvantages. It explores how consistent policy enforcement can safeguard cloud
environments from cyber threats and how Zero Trust principles can minimize attack surfaces. Furthermore, the study highlights ZTA’s role in mitigating ransomware attacks and reducing vendor risks, ultimately presenting a robust approach for securing multi-cloud ecosystems.
In simple terms a zero-trust environment does not make any assumptions about the trustworthiness of users. Instead, it uses a “least privilege” approach in which users are only given the least privilege access that they need to do their job and no more. This approach can help organizations improve their cybersecurity posture by making it more difficult for attackers to access sensitive data. It also simplifies security management by eliminating the need to manage complex firewall rules.
In contrast, in a traditional trust-based environment, organizations typically have perimeter-based security that relies on firewalls and other security controls to keep the bad guys out.
Zero-trust environments are often considered more secure than traditional trust-based ones, but some tradeoffs must be considered. For example, zero-trust environments can require more effort to set up and manage and may not be compatible with all legacy applications
1. Introduction
As organizations increasingly adopt multi-cloud strategies to leverage diverse capabilities and services, ensuring robust security across these platforms has become paramount. Traditional perimeter-based security models are inadequate in such dynamic environments, where data and workloads are distributed across multiple cloud service providers. Zero Trust Architecture (ZTA) offers a paradigm shift by enforcing a “never trust, always verify” approach [1] , focusing on continuous validation of user and device identity, granular access controls, and comprehensive monitoring.
This paper investigates the application of ZTA in multi-cloud environments, emphasizing the importance of consistent policy enforcement. It examines how adopting ZTA can address vulnerabilities, reduce the attack surface, and enhance protection against sophisticated threats such as ransomware. The study also evaluates potential disadvantages and provides insights into mitigating vendor risks within a multi-cloud context.

Overview of ZTA
Figure A : Overview Of Zero Trust
2. Literature Survey – The Evolution of Enterprise Security: From Perimeter to Zero Trust
The concept of Zero Trust was first introduced by Forrester Research in 2010, emphasizing the need for granular access controls and identity verification. Studies have demonstrated that traditional security models struggle to adapt to multi-cloud architectures due to fragmented policies and inconsistent enforcement mechanisms.
2.1 Pre-2004: The Era of Perimeter-Based Security
For decades, enterprise security relied on the perimeter-based approach, modeled after a “castle and moat” philosophy. Organizations built strong external defenses—firewalls, intrusion detection systems, and access controls—to protect internal resources.
Within this model, anyone inside the perimeter (e.g., employees, devices on internal networks) was implicitly trusted, while external entities were viewed as untrusted. This approach worked well in environments where resources were centralized in on-premises data centers, and access was primarily through local office networks.
However, the early 21st century brought a seismic shift:
- Cloud Adoption: Enterprises began moving their infrastructure, applications, and data to cloud platforms.
- Decentralization: Workforces became more distributed, with employees working from remote locations and using personal devices.
- Evolving Threats: Cyberattacks grew more sophisticated, often exploiting implicit trust within internal networks.[8]
These changes made traditional perimeter defenses inadequate, as threats could easily bypass
them once inside.
2.2 2004: The Foundations of Zero Trust – Deperimeterization
In 2004, the Jericho Forum, an international consortium of security professionals, foresaw the limitations of perimeter-based defenses. They introduced the concept of deperimeterization, advocating for security models that no longer depended on a defined boundary.
Key principles of de-perimeterization included:
- Data-Centric Security: Protecting data itself, regardless of where it resides.
- Encryption: Ensuring data is encrypted in transit and at rest.
- Identity-Based Controls: Authenticating users and devices based on their identity rather than their location.
This forward-thinking approach recognized the growing mobility of users and data, laying the groundwork for the Zero Trust philosophy.
2.3 2010: The Birth of “Zero Trust”
John Kindervag, then a principal analyst at Forrester Research, coined the term Zero Trust in 2010. He formalized it as a response to the inherent weaknesses of perimeter-based security.
Kindervag’s core assertion was simple yet revolutionary:
“Trust is a vulnerability.”
Rather than granting implicit trust to users or devices within the network, Zero Trust assumes that every interaction is potentially malicious. It enforces strict identity verification and access controls at every point, regardless of the user’s location or device.
2.4 The Shift to Zero Trust: Why It Matters
The traditional perimeter-based approach became ineffective in addressing modern challenges:
- Remote Work: Employees accessing corporate resources from home or public networks increased the attack surface.
- Cloud Computing: Data and applications moved outside the physical network perimeter, making it harder to enforce consistent protections.
- BYOD (Bring Your Own Device): The proliferation of personal devices accessing enterprise networks introduced unmanaged endpoints.
- Sophisticated Threats: Attackers increasingly exploited lateral movement within networks, abusing the implicit trust granted to “insiders.”
Zero Trust addressed these gaps by adopting the principle of least privilege access:
- Users and devices are granted the minimum permissions necessary to perform their tasks.
- Access is verified continuously, using real-time context such as user identity, device health, location, and behavior.[9]
2.5 Core Principles of Zero Trust
Zero Trust is built on several foundational pillars: [10]
1. Verify Explicitly
- Always authenticate and authorize access using all available data points, such as user identity, device health, location, and behavior.
- Implement strong authentication mechanisms like Multi-Factor Authentication (MFA) and continuous verification to minimize risks.
2. Use Least Privilege Access
- Grant users and devices the minimum level of access necessary to perform their tasks.
- Regularly review and adjust permissions to ensure access aligns with business needs and security policies.
- Enforce just-in-time (JIT) and just-enough-access (JEA) controls to reduce exposure.
3 . Assume Breach
- Design systems under the assumption that an attacker may already be inside the network.
- Employ segmentation to minimize lateral movement, limiting the scope of potential damage.
- Continuously monitor and log activity to detect and respond to anomalies in real time.
4. Microsegmentation
- Divide the network into smaller, secure zones to isolate workloads and applications.
- Implement granular access controls within these segments to reduce the attack surface.
5. Continuous Monitoring and Analytics
- Utilize real-time data collection and analysis to detect potential threats and unauthorized access.
- Leverage AI and machine learning for behavior analytics and anomaly detection.
6. Context-Aware Policies
- Apply dynamic access policies based on contextual factors such as device posture, geolocation, and time of access.
- Adapt security controls based on the current risk level of the interaction.
7. End-to-End Encryption
- Ensure data is encrypted at rest and in transit, reducing exposure to interception or tampering.
- Implement data integrity measures to prevent unauthorized modifications.
8. Secure Access to All Resources
- Apply consistent security controls across all environments, including on-premises, cloud, and hybrid setups.
- Protect all endpoints, applications, and APIs with a uniform security strategy.
9. Automation and Orchestration
- Use automated tools to enforce policies, respond to threats, and maintain compliance with minimal manual intervention.
- Integrate security workflows across diverse systems for seamless policy enforcement.
10. Zero Trust Network Access (ZTNA)
- Replace traditional VPNs with ZTNA solutions that verify each connection individually, ensuring secure access to specific applications without exposing the broader network.
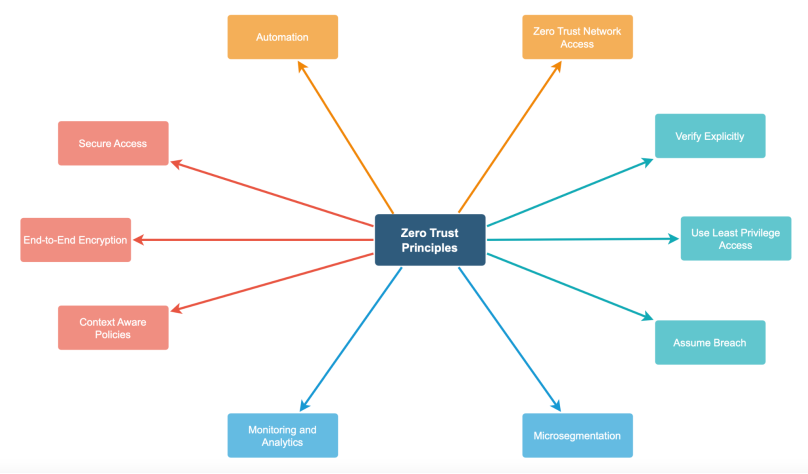
Zero Trust Principles
Figure B : Principles Of Zero Trust
2.6 Key Technologies Enabling Zero Trust
The implementation of Zero Trust often relies on:
- Identity and Access Management (IAM): Centralized user authentication and authorization.
- Multi-Factor Authentication (MFA): Adding layers of verification to prevent unauthorized access.
- Microsegmentation: Dividing networks into smaller zones to limit the spread of threats.
- Endpoint Detection and Response (EDR): Monitoring and responding to suspicious activity on devices.
- Cloud Access Security Brokers (CASBs): Ensuring secure access to cloud applications. [9]
2.7 Zero Trust in Practice
Adopting Zero Trust requires cultural, procedural, and technological shifts:
- Cultural Change: Organizations must move away from legacy trust models and embrace the idea of continuous verification.
- Continuous Monitoring: Real-time analysis of user behavior and device health to detect anomalies.
- Policy Enforcement: Automated policies based on context, ensuring consistent security across on-premises and cloud environments.
- 2.8 The Future of Zero Trust
As organizations increasingly adopt hybrid work models and multi-cloud strategies, Zero Trust continues to evolve. Emerging technologies like AI and machine learning are enhancing the ability to detect threats and enforce policies dynamically.[2]
By shifting the focus from “trusted” networks to context-aware access and continuous validation, Zero Trust represents the modern standard for enterprise security.
2.9 Key Research Contributions:
- Sharma et al. (2021): Explored ZTA’s effectiveness in mitigating insider threats, showcasing its ability to limit unauthorized access and reduce the impact of malicious actions within organizations.
- Lee et al. (2022): Investigated ZTA’s application in securing distributed workloads, emphasizing micro-segmentation and continuous monitoring to counteract lateral movement within cloud environments.
- NIST SP 800-207 (2020): Provided foundational guidance on implementing ZTA, outlining principles like least privilege and identity-based access controls.
2.10 Industry Practices:
- Microsoft Azure (2023): Highlighted ZTA’s application in multi-cloud environments, offering insights into tools and services designed for consistent policy enforcement.
- Google Cloud and AWS: Documented their respective ZTA models, emphasizing interoperability and vendor-agnostic frameworks for unified security.[6]
Despite these advancements, challenges persist in implementing ZTA across multi-cloud environments. Fragmented security policies and lack of standardization remain critical barriers, necessitating a structured and comprehensive framework.
3. Methodology
The proposed framework integrates Zero Trust principles with policy enforcement mechanisms to secure multi-cloud environments. The methodology comprises six core components:
3.1 Identity-Centric Access Controls
Identity is the cornerstone of ZTA. Authentication and authorization are enforced through:
- Multi-Factor Authentication (MFA): Ensuring users verify their identity through multiple channels.
- Identity as a Service (IDaaS): Centralized identity management tools like Azure AD and Okta.[5]
Example Code: Configuring MFA in Azure AD:

Azure commandline MFA
Figure C : Multi-Factor Authentication in Azure
3.2 Dynamic Policy Enforcement
Dynamic policies are enforced using centralized policy engines, incorporating:
- Risk-Based Access Control (RBAC): Adjusting access based on real-time threat analysis.
- Tools: Azure Policy, AWS Organizations, and Terraform.[5]
Example Policy Definition (Terraform):

Azure commandline policy
Figure D : Policy Definition in Azure
3.3 Micro-Segmentation
Breaking down the network into smaller, isolated segments limits lateral movement.
Tools:
- VMware NSX for micro-segmentation.
- AWS Security Groups for controlling inbound and outbound traffic.[7]
Example: Configuring security groups in AWS:
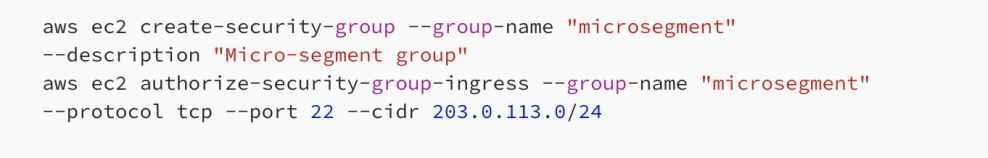
AWS ommandline security groups
Figure E : Security Groups in AWS
3.4 Continuous Monitoring
Continuous monitoring ensures prompt detection of anomalies using:
- Security Information and Event Management (SIEM): T ools like Splunk and Azure Sentinel.
- Behavioral Analytics: Leveraging AI/ML to identify deviations.
Example: Integrating Azure Sentinel with continuous monitoring:

Azure commandline tomonitor
Figure F : Monitoring in Azure
3.5 Ransomware Mitigation Techniques
Mitigation strategies include:
- Immutable Backups: Preventing backup tampering.
- Encryption: Ensuring sensitive data is unreadable without keys.
- Incident Response: Automated responses to ransomware detections.[4]
3.6 Vendor Risk Management
Third-party risks are minimized through:
- Audits: Regularly evaluating vendor compliance.
- Contractual Requirements: Mandating adherence to ZTA principles.
- Continuous Assessment: Monitoring vendors for emerging risks.
4. Results and Discussion
4.1 Advantages of ZTA in Multi-Cloud Environments
- Improved Security Posture: ZTA reduces risks by enforcing strict identity-based access.
- Minimized Attack Surface: Micro-segmentation and least privilege principles limit entry points.
- Ransomware Resilience: Immutable backups and encryption ensure data integrity.
- Vendor Risk Reduction: Unified security policies mitigate third-party risks.[3]
4.2 Challenges in Adopting ZTA
Complexity: Deploying ZTA across multi-cloud environments requires expertise.
- Performance Overheads: Continuous monitoring impacts system performance.
- Cost Implications: Investments in tools and expertise are significant.
- Case Study: Implementation of ZTA in a Several Industries:
Microsoft: Zero Trust for Enterprise Modernization
- Context: Microsoft transitioned to a Zero Trust model to protect its global hybrid cloud environment and workforce.
- Solution: They adopted a company-wide Zero Trust strategy focused on identity, device, and workload protection.
- Key Implementations:
- Identity as a Control Plane: Multi-Factor Authentication (MFA) and Conditional Access for all users.
- Device health monitoring with Endpoint Manager and Defender for Endpoint.
- Microsegmentation of networks to contain potential breaches.
- Outcome: Enhanced protection for 130,000+ employees and partners while enabling seamless access to critical resources across cloud and on-premises systems.[11]
U.S. Department of Defense (DoD): ZTNA Pilot Program
- Context: The DoD faced increasing cyber threats targeting its vast and complex infrastructure, including classified and unclassified systems.
- Solution: Initiated a pilot program to implement Zero Trust Network Access (ZTNA) across critical systems.
- Key Implementations:
- Adopted identity-centric security controls, ensuring that only authenticated and authorized users could access sensitive data.
- Microsegmentation for secure access to specific applications, reducing attack vectors.
- Real-time monitoring and incident response capabilities.
- Outcome: Strengthened the defense of mission-critical systems and established a scalable model for broader Zero Trust adoption across federal agencies.13]
Healthcare Provider: Securing Patient Data
- Context: A large healthcare organization faced challenges in protecting sensitive patient data across multiple locations and cloud platforms.
- Solution: Adopted Zero Trust to secure electronic health records (EHRs) and ensure compliance with HIPAA regulations.
- Key Implementations:
- Identity-based access controls for healthcare staff and contractors.
- Data encryption for all patient records, both at rest and in transit.
- Continuous monitoring to detect insider threats and unauthorized access attempts.
- Outcome: Improved compliance and security posture while enabling secure remote access for telehealth services.[12]
Google: BeyondCorp
- Context: Google experienced a sophisticated cyberattack in 2010 (Operation Aurora), which highlighted vulnerabilities in its perimeter-based security model.
- Solution: Google developed BeyondCorp, a Zero Trust framework to secure internal applications and services. [6]
- Key Implementations:
- Replaced traditional VPNs with a model that verifies every user and device before granting access.
- Implemented device certificates and strict identity-based access controls.
- Integrated continuous monitoring to detect and mitigate threats dynamically.
- Outcome: Employees gained secure access to resources from any location without relying on traditional network perimeters, significantly reducing the risk of lateral movement in the event of a breach.
Netflix: Protecting a Distributed Environment
- Context: Netflix’s global operations and reliance on microservices required a security model capable of scaling across distributed environments.
- Solution: Implemented Zero Trust principles for securing service-to-service communication and user access. [14]
- Key Implementations:
- Built an internal system called LEMUR for service identity and certificate management.
- Enforced strong encryption and mutual TLS (mTLS) for all internal communications.
- Implemented microsegmentation to isolate workloads within their cloud environment.
- Outcome: Enhanced security for millions of daily transactions while maintaining operational efficiency.
5. Conclusion
The adoption of multi-cloud environments has fundamentally transformed how organizations manage and secure their IT infrastructure. Traditional perimeter-based security models are no longer effective in addressing the complexities of distributed architectures, dynamic workloads, and an increasingly sophisticated threat landscape. In response to these challenges, the Zero Trust framework has emerged as a robust security paradigm, emphasizing continuous verification, least privilege access, and the principle of “never trust, always verify.”
Implementing Zero Trust in multi-cloud environments requires a cohesive strategy that ensures consistent policy enforcement across diverse platforms and services. Organizations must leverage identity and access management (IAM), microsegmentation, and real-time monitoring to maintain granular control over user and device interactions. Additionally, adopting a unified security policy framework allows for streamlined governance and compliance, even in heterogeneous cloud ecosystems.
While the transition to Zero Trust demands significant cultural, technical, and operational shifts, the benefits far outweigh the challenges. By embedding security into every layer of the infrastructure and enforcing contextual, identity-driven access policies, organizations can mitigate risks and build resilience against evolving cyber threats.
In conclusion, Zero Trust is not merely a security strategy but a foundational framework for securing multi-cloud environments. Its principles of continuous verification and adaptive security are essential for navigating the complexities of modern enterprise IT , ensuring that organizations can achieve their goals without compromising on security. The future of multi-cloud security lies in embracing Zero Trust as a strategic enabler for innovation and business continuity.
6. References
1. Forrester Research. (2010). “The Zero Trust Model of Information Security.”
2. Sharma, P ., & Gupta, R. (2021). “Zero Trust in Cloud Computing: Mitigating Insider Threats. ” Journal of Cloud Security, 14(3), 45-56.
3. Lee, J., & Park, S. (2022). “Securing Distributed Workloads with Zero Trust.” International Journal of Cybersecurity, 9(1), 78-90.
4. National Institute of Standards and T echnology (NIST). (2020). “Zero Trust Architecture.” SP 800-207.
5. Microsoft Azure. (2023). “Zero Trust in Multi-Cloud Environments.” White Paper.
6. Google Cloud. (2022). “Adopting Zero Trust for Multi-Cloud Strategies.
“7. Amazon Web Services (AWS). (2022). “Implementing Zero Trust in Cloud-Native Applications.”
8. Theory and Application of Zero Trust Security: A Brief Survey : https://pmc.ncbi.nlm.nih.gov/articles/PMC10742574/
9. PaloAlto Networks (2024). ”The State of Cloud-Native Security 2024 Report”
10. American Public University (2022) : Zero Trust Cybersecurity and Why You Should Care about It.
11. Microsoft Security : Zero Trust Strategy & Architecture | Microsoft Security
12. HHS Cyber security Program (2020): Zero Trust In Healthcare
13. U.S Department Of Defence (2022): DoD Zero Trust Strategy
14. Research Gate (2024): Zero Trust Architecture: Redefining Security Paradigms In The Digital Age
Keywords: Zero Trust Security, Automation, Software Development, Security, Least Privilege, Multi Cloud Security, MicroSegmentation
